Cloud Security
Cloud hosting security is crucial to ensure the confidentiality, integrity, and availability of data and services in cloud environments. Given the shared nature of cloud resources, security in cloud hosting involves both provider-side and customer-side measures. Here’s a comprehensive look at cloud hosting security:
Cloud Security
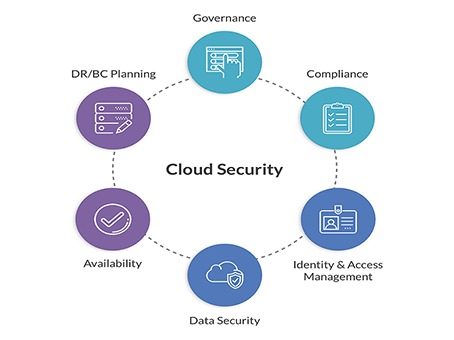
Shared Responsibility Model:
- Provider Responsibility: Cloud service providers (CSPs) are responsible for securing the infrastructure, including hardware, networking, and the virtualization layer.
- Customer Responsibility: Customers are responsible for securing their data, applications, and configurations within the cloud environment.
Access Control:
- Identity and Access Management (IAM): Implement strong IAM policies to manage user permissions and access to resources. Use Multi-Factor Authentication (MFA) for additional security.
- Role-Based Access Control (RBAC): Assign permissions based on roles to minimize excessive access rights.
Data Protection:
- Encryption: Encrypt data at rest (stored data) and in transit (data being transferred). Use strong encryption standards and manage encryption keys securely.
- Data Masking: Mask sensitive data to protect it from unauthorized access, especially in non-production environments.
Network Security:
- Firewalls: Use cloud-native firewalls or security groups to control inbound and outbound traffic.
- Virtual Private Network (VPN): Use VPNs to secure communication between your on-premises environment and the cloud.
- Intrusion Detection and Prevention Systems (IDPS): Implement IDPS to monitor and protect against potential threats.
Compliance and Governance:
- Compliance Standards: Ensure adherence to industry standards and regulations like GDPR, HIPAA, and PCI-DSS.
- Audit Logs: Maintain and review audit logs to track access and changes to resources.
Backup and Disaster Recovery:
- Regular Backups: Schedule regular backups and ensure they are stored securely and are easily retrievable.
- Disaster Recovery Plan: Develop and test a disaster recovery plan to ensure business continuity in case of a major failure.
Security Monitoring and Incident Response:
- Monitoring Tools: Use cloud-native monitoring tools and third-party solutions to detect and respond to security threats.
- Incident Response Plan: Establish and regularly update an incident response plan to address potential security incidents promptly.
Secure Configuration:
- Configuration Management: Follow best practices for securely configuring cloud resources and services.
- Hardening: Apply security hardening practices to reduce vulnerabilities in operating systems and applications.
Best Practices:
- Understand the Shared Responsibility Model: Know what your provider secures and what you need to manage.
- Regularly Review Security Policies: Update security policies and practices to adapt to new threats and changes in your cloud environment.
- Educate and Train Staff: Provide regular security training for staff to recognize and respond to security threats.
- Use Security Tools and Services: Leverage tools provided by cloud vendors and third-party security solutions to enhance your security posture.
Popular Cloud Security Tools:
- AWS Security Hub: Centralizes security alerts and compliance status across AWS accounts.
- Azure Security Center: Provides unified security management and advanced threat protection across Azure and on-premises.
- Google Cloud Security Command Center: Offers centralized security and data risk management for Google Cloud.
- Cloudflare: Provides a range of security solutions, including DDoS protection and web application firewall (WAF).
Emerging Trends in Cloud Security:
- Zero Trust Architecture: Emphasizes never trusting and always verifying user identities and devices, regardless of location.
- Artificial Intelligence and Machine Learning: Used for advanced threat detection and response.
- Serverless Security: Focuses on securing serverless architectures and functions.
Cloud hosting security is a multifaceted approach that involves protecting your data, applications, and infrastructure through a combination of technologies, practices, and policies. By implementing these measures and staying informed about new threats and technologies, organizations can enhance their security posture in cloud environments.
24x7 Online Expert Support
